Generate Public Key From Priveate
14.12.2020 admin
- You cannot generate private key from public key but you can generate public key from the private key using puttygen. As @alfasin mentioned if you could generate the private key from public key then RSA would be useless and this would make you vulnerable to attack.FYI the public key is used for encryption and private key is used for decryption.
- Jul 09, 2019 The Private Key is generated with your Certificate Signing Request (CSR). The CSR is submitted to the Certificate Authority right after you activate your Certificate. The Private Key must be kept safe and secret on your server or device, because later you’ll need it for Certificate installation.
- To generate the public/private key pair, enter this in the Command Prompt: ssh-keygen At the first prompt, “Enter file in which to save the key,” press Enter to save it in the default location.
- Generating the Private Key - Linux 1. Open the Terminal. Navigate to the folder with the ListManager directory. Type the following: openssl genrsa -out rsa.private 1024 4. The private key is generated and saved in a file named 'rsa.private' located in the same folder. Generating the Public Key - Linux 1. Open the Terminal.
- To generate the missing public key again from the private key, the following command will generate the public key of the private key provided with the -f option. $ ssh-keygen -y -f /.ssh/idrsa /.ssh/idrsa.pub Enter passphrase: The -y option will read a private SSH key file and prints an SSH public key to stdout. The public key part is redirected to the file with the same name as the private key.
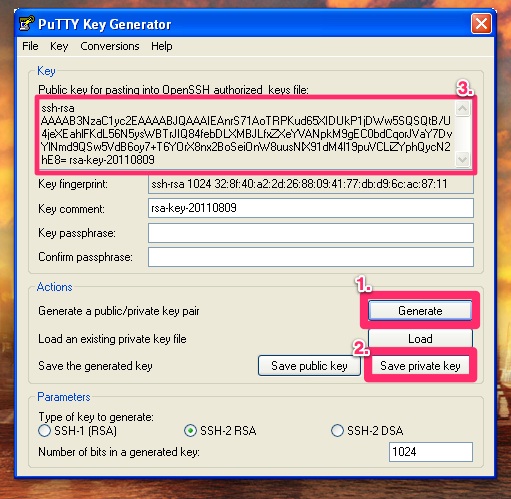
Generate online private and public key for ssh, putty, github, bitbucket. Save both of keys on your computer (text file, dropbox, evernote etc)! The generated keys are random/unique and we can't restore a missing key. You will need to copy/set the public key on to the remote server/service. Jul 09, 2019 The Private Key is generated with your Certificate Signing Request (CSR). The CSR is submitted to the Certificate Authority right after you activate your Certificate. The Private Key must be kept safe and secret on your server or device, because later you’ll need it for Certificate installation.
Encryption is a process of embedding plain text data in such a way that it cannot be decoded by outsiders. It is necessary to encrypt data to prevent misuse. The GNU Privacy Guard (GPG) application allows you to encrypt and decrypt information. It is based on the use of a pair of keys, one public and one private (or secret). Data encrypted with one key can only be decrypted with the other. To encrypt a message to you, someone would use your public key to create a message that could only be unlocked with your private key. To sign information, you would lock it with your private key, allowing anyone to verify that it came from you by unlocking it with your public key.
Modern Linux distributions have gpg already installed on them. If not present, install it.
on Centos
on Ubuntu
1) Create gpg key
When installing gnupg package, we need to understand the concept to use gpg as well.
Generating a new keypair
To encrypt your communication, the first thing to do is to create a new keypair. GPG is able to create several types of keypairs, but a primary key must be capable of making signatures.
uid:Please take a note about the USER-ID mentioned in the result. We will use its value to do some operation.pub:It represents the public key. The key-id is BAC361F1. Yours will be differentsub:It represents subkeys, goes along with the primary key. Commonly, it is used to encryption.
Your prompt can be handled for a very long time without finishing if you see the message below
'Not enough random bytes available. Please do some other work to give
the OS a chance to collect more entropy! (Need 285 more bytes)'
The problem is caused by the lack of entropy (or random system noise). So cancel the process and check the available entropy
You can see it is not enough. We can install a package to solve the lack of entropy with rngd which is a random number generator utility used to check immediately the available entropy
Now can start again with the gpg --gen-key command and the process will be fine. We have only installed it without anything else. In certain distributions, you need to use rngd before the gpg process.
3) Generating a revocation certificate
After your keypair is created you should immediately generate a revocation certificate to revoke your public key if your private key has been compromised in any way or if you lose it. Create it when you create your key. The process requires your private key, passphrase.
The argument BAC361F1 is the key ID. It must be a key specifier, either the key ID of your primary keypair or any part of a user ID that identifies your keypair like my_name@linoxide.com. The generated certificate will be saved in revoke_key.asc file. Store it where others can't access it because anybody having access to it can revoke your key, rendering it useless. If the --output option is omitted, the result will be placed on standard output.
4) Making an ASCII armored version of your public key
Some keyservers allow you to paste an ASCII armored version of your public key in order to upload it directly. This method is most preferred because the key comes directly from the user who can see that the key has been successfully uploaded.
5) Exchanging keys
In order to communicate with others, you must exchange public keys. To do it, you must be able to list your keys. There is some commands to list your public keyring
gpg --list-keys:List all keys from the public keyrings, or just the keys given on the command line.gpg --list-secret-keys:List all keys from the secret keyrings or just the ones given on the command linegpg --list-sigs:Same as --list-keys, but the signatures are listed too.
Export a public key
Now that you have generated a key pair, the next step is to publish your public key on internet ( Keyservers ) so that other person can use it to send you a message. You can use either the key ID or any part of the user ID may be used to identify the key to export. There are two commands but with the first command, the key is exported in a binary format and can be inconvenient when it is sent through email or published on a web page. So, we will use the second command for ASCII armored method. /monster-hunter-generations-ultimate-key-quests-multiplayer.html.
The output will be redirected to my_pubkey.gpg file which has the content of the public key to provide for communication.
Submit your public keys to a keyserver
Openssl Generate Public Private Key
Once you have this ASCII-armored public key, you can manually paste it into a form at a public key server like pgp.mit.edu
Because someone seems to have sent you their public key, there's no reason to trust that it's from that person unless you have validated it.
Import a public key
As others persons can use your public key to send you a message, you can import public from people you trust in to communicate with them.
Conclusion
Now we have notions on the principles to use and generate a public key. You know how GnuPG is functioning and you can use it for secure communication. GPG encryption is only useful when both parties use good security practices and are vigilant.
Read Also:
While Encrypting a File with a Password from the Command Line using OpenSSLis very useful in its own right, the real power of the OpenSSL library is itsability to support the use of public key cryptograph for encrypting orvalidating data in an unattended manner (where the password is not required toencrypt) is done with public keys.
The Commands to Run
Generate a 2048 bit RSA Key
Generate private key openssl online. You can generate a public and private RSA key pair like this:
openssl genrsa -des3 -out private.pem 2048
That generates a 2048-bit RSA key pair, encrypts them with a password you provideand writes them to a file. You need to next extract the public key file. You willuse this, for instance, on your web server to encrypt content so that it canonly be read with the private key.
Export the RSA Public Key to a File
This is a command that is
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
The -pubout flag is really important. Be sure to include it.
Next open the public.pem and ensure that it starts with-----BEGIN PUBLIC KEY-----. This is how you know that this file is thepublic key of the pair and not a private key.
To check the file from the command line you can use the less command, like this:
less public.pem
Do Not Run This, it Exports the Private Key
A previous version of the post gave this example in error.
openssl rsa -in private.pem -out private_unencrypted.pem -outform PEM
The error is that the -pubout was dropped from the end of the command.That changes the meaning of the command from that of exporting the public keyto exporting the private key outside of its encrypted wrapper. Inspecting theoutput file, in this case private_unencrypted.pem clearly shows that the keyis a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----.
Visually Inspect Your Key Files
It is important to visually inspect you private and public key files to makesure that they are what you expect. OpenSSL will clearly explain the nature ofthe key block with a -----BEGIN RSA PRIVATE KEY----- or -----BEGIN PUBLIC KEY-----.

You can use less to inspect each of your two files in turn:
less private.pemto verify that it starts with a-----BEGIN RSA PRIVATE KEY-----less public.pemto verify that it starts with a-----BEGIN PUBLIC KEY-----
The next section shows a full example of what each key file should look like.
The Generated Key Files
The generated files are base64-encoded encryption keys in plain text format.If you select a password for your private key, its file will be encrypted withyour password. Be sure to remember this password or the key pair becomes useless.
The private.pem file looks something like this:
The public key, public.pem, file looks like:
Protecting Your Keys
Depending on the nature of the information you will protect, it’s important tokeep the private key backed up and secret. The public key can be distributedanywhere or embedded in your web application scripts, such as in your PHP,Ruby, or other scripts. Again, backup your keys!
Remember, if the key goes away the data encrypted to it is gone. Keeping aprinted copy of the key material in a sealed envelope in a bank safety depositbox is a good way to protect important keys against loss due to fire or harddrive failure.
Oh, and one last thing.
If you, dear reader, were planning any funny business with the private key that I have just published here. Know that they were made especially for this series of blog posts. I do not use them for anything else.
Found an issue?
Rietta plans, develops, and maintains applications.
Learn more about our services or drop us your email and we'll e-mail you back.